Introduction
A legal hold is not merely a procedural formality. It is a critical obligation tied directly to legal hold compliance, document preservation, and overall litigation readiness. When mishandled, organizations face severe ediscovery sanctions, including multi-million-dollar penalties and damaging adverse inferences that can decide entire cases.
Despite the risks, many companies still treat the litigation hold as a checkbox task rather than a strategic compliance initiative. True legal defensibility is achieved not by luck, but by consistent adherence to litigation hold best practices and the steps for defensible preservation legal holds outlined below.

Strategy 1: Establish Clear Triggers and Early Litigation Hold Protocols
A defensible legal hold procedure begins before the first notice is issued. Defining early triggers improves legal hold compliance and strengthens corporate governance litigation posture.
The Trigger Event for a Legal Hold
The foundational question is simple: When must a legal hold be issued? The answer is legally complex: when litigation is “reasonably anticipated.” This is where many organizations falter. What circumstances trigger reasonable anticipation?
Common triggers include:
- Receipt of a cease-and-desist letter or demand letter
- Notice of a government investigation or regulatory inquiry
- Termination of an employee who has indicated an intention to sue
- Discovery of potential regulatory violations
- Actual commencement of litigation
- Board-level discussion of potential litigation risk
The critical insight is that you don’t need actual litigation to trigger a legal hold. The standard is “reasonable anticipation,” which courts interpret broadly. An organization that waits for formal litigation to commence before issuing a hold may already be in violation.
Developing Hold Trigger Protocols
Organizations should document:
- 1. Specific triggering events: - What circumstances necessitate a hold?
- 2. Decision timeline - Within how many hours/days must legal review the matter?
- 3. Escalation procedures - Who has the authority to declare a hold?
- 4. Cross-functional communication- Who must be notified?
- 5. Documentation preservation- What records must be created?
The protocol itself becomes evidence of organizational culture around compliance. When litigation occurs, you can demonstrate that holds weren’t reactionary but part of systematic procedures. This transforms your legal hold from suspicious to defensible.
Many organizations fail this strategy because they lack clear protocols. If different departments independently decide when holds should commence, inconsistency invites challenge. If a senior executive can unilaterally dismiss a potential litigation matter, you risk missing holds. Documented, systematic protocols eliminate these weaknesses.
Strategy 2: Comprehensive Custodian Identification in the Litigation Hold Process
The scope of a legal hold depends critically on identifying the right custodians, individuals who may possess responsive information. This requires systematic analysis and documented procedures.
Custodian Identification Methodology
Defensible holds identify custodians through:
- Organizational structure review - Who holds relevant positions?
- Party analysis - Who was directly involved in disputed transactions or events?
- Communication pattern analysis - Who was communicating about the subject matter?
- Document repository mapping - Where might relevant information exist?
- Testimony from key witnesses - Who would have relevant knowledge?
The critical point: identification should be documented and reasoned. If a legal team decides not to include certain custodians in a hold, that decision should be recorded with a rationale. This demonstrates that inclusion/exclusion was deliberate, not accidental.
Hold Notice Best Practices
Once custodians are identified, notification procedures significantly impact defensibility:
- Written notice – Hold notices must be in writing, not verbal
- Specific scope – Describe exactly what must be preserved (emails, documents, messages, files)
- Functional descriptions – Describe by subject matter, not just “litigation-related materials”
- Custodian-specific tailoring – Different custodians may need different holds based on their role
- Preservation methodology – Explain how to preserve (backup email, save files, etc.)
- Acknowledgment mechanism – Require signed certification that custodians understand
- Multiple contact methods – Send notice via email, in-person meeting, and internal system
- Translation if necessary – Translate notices for non-English speakers
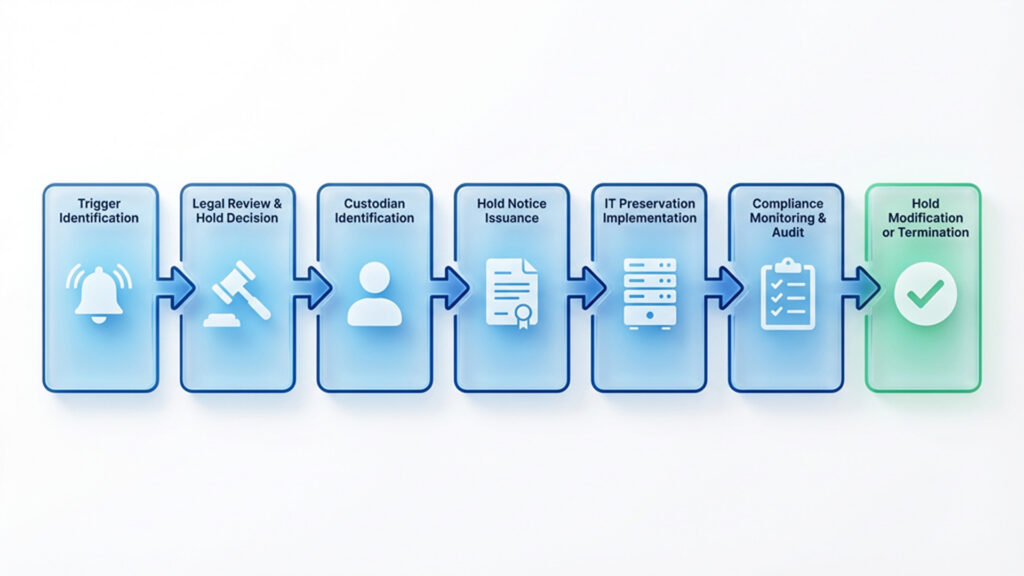
Communication Protocol Example
A defensible hold notice includes language such as:
"You are required to preserve all documents, emails, instant messages, text messages, and electronically stored information (ESI) relating to [describe dispute/matter] from [date] forward. This includes information on your work computer, personal devices used for work, cloud storage, backup devices, and any other storage location. Please preserve by: [specific preservation instructions]. You must acknowledge receipt of this notice within 24 hours by [method]. Failure to comply may result in sanctions, adverse inferences, and litigation consequences."
A detailed legal hold notice clarifies obligations and prevents confusion, reinforcing legal defensibility and improving corporate governance litigation credibility.
Strategy 3: Documentation for Legal Hold Compliance and Legal Defensibility
Perhaps more than any other factor, documentation distinguishes defensible holds from indefensible ones. The legal hold file becomes your evidence that you acted reasonably and systematically.
Components of a Defensible Hold File
Your legal hold documentation should include:
- Organizational structure review - Who holds relevant positions?
- Party analysis - Who was directly involved in disputed transactions or events?
- Communication pattern analysis - Who was communicating about the subject matter?
- Document repository mapping - Where might relevant information exist?
- Testimony from key witnesses - Who would have relevant knowledge?
A. Trigger Documentation
- What event triggered the hold?
- When was legal counsel notified?
- What analysis was performed to determine reasonable anticipation of litigation?
- Who made the decision to issue a hold?
B. Scope Determination
- What is the legal matter?
- What time period is covered?
- What custodians are included and why?
- What types of information must be preserved?
- Are there excluded categories (attorney-client privilege, work product)?
C. Hold Notice Communication
- Copies of the hold notice(s) issued
- Distribution lists showing who received notice
- Proof of delivery or acknowledgment
- Any follow-up communications
- Responses or questions from custodians
D. Compliance Verification
- Certification from IT confirming that holds were implemented
- Audit results showing compliance
- Any exceptions or issues that arose
- How exceptions were resolved
E. Modification Records
- When and why the hold was modified
- Documentation of scope expansion or contraction
- Approval for any modifications
- Communication of modifications to custodians
F. Termination Records (when applicable)
- When was the hold terminated?
- What circumstances justified termination?
- How were custodians notified?
- Approval for termination
The Contemporaneous Documentation Standard
Once custodians are identified, notification procedures significantly impact defensibility:
Courts give significant weight to contemporaneous documentation, records created at the time of the hold decision, not months later when litigation has commenced. A hold file created as the hold is issued carries more weight than a reconstructed file created during discovery.
This is why forward-thinking organizations implement legal hold platforms that automatically generate documentation as holds are issued, modified, and managed. The timestamped, contemporaneous record becomes powerful evidence of systematic compliance.
Legal Hold Defensibility Checklist
Ensure your hold process can withstand judicial scrutiny
Download our comprehensive checklist covering all elements of a defensible legal hold. Use it to audit your current process and identify gaps before litigation arrives.
- Trigger identification requirements
- Custodian identification methodology
- Hold notice content requirements
- Documentation requirements
- Compliance verification procedures
- Modification tracking
- Termination procedures
- Common pitfalls to avoid
Strategy 4: Establish IT Integration and Technical Preservation Protocols
A legal hold is only as good as its technical implementation. Excellent policy matters little if IT systems don’t actually preserve the targeted information. That’s why technology plays a decisive role in automating legal hold workflows and protecting ESI integrity.
Critical IT Integration Points
Defensible holds require deep integration between legal and IT:
Email Preservation
- Identify email systems (Exchange, Gmail, etc.)
- Implement litigation hold flags in email systems
- Prevent deletion of flagged emails
- Document which email accounts are placed on hold
- Verify technical hold is active in system logs
File System Preservation
- What is the legal matter?
- Identify file storage locations (network drives, OneDrive, SharePoint)
- Implement deletion restrictions on hold folders
- Document which file systems are under hold
- Create regular backups of hold-targeted data
- Verify backup integrity
Mobile Device and Personal Computer Preservation
- Establish procedures for mobile devices (iPhones, Android)
- Require preservation of personal computers if work-related data exists
- Document device inventory under hold
- Create forensic images where appropriate
Cloud Storage and Third-Party Systems
- Identify all cloud services used (Slack, Teams, Box, Dropbox, etc.)
- Communicate hold requirements to service providers
- Document holds in each platform
- Verify service provider compliance
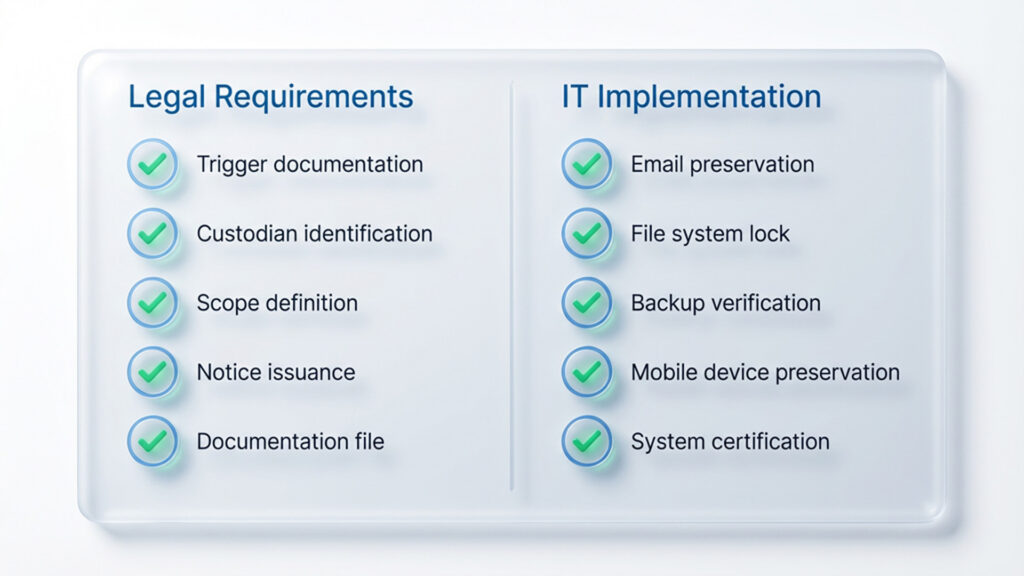
The IT Certification Protocol
A critical legal defensibility element: IT should provide written certification that:
- Hold instructions were received and understood
- Preservation measures were implemented
- Preservation measures remain active
- Specific systems/accounts are under preservation
- Any technical limitations or exceptions exist
This certification becomes crucial evidence. It demonstrates not just that legal issued a hold, but that IT actually implemented it. Without IT documentation, a hold notice alone proves nothing about actual preservation.
Common IT Integration Failures
Organizations frequently fail this strategy by:
- Issuing hold notices without IT coordination
- Assuming legal hold notices are self-executing (they’re not)
- Failing to follow up on IT implementation
- Not addressing newer communication platforms
- Neglecting to verify that holds remain active over time
- Failing to coordinate holds during system upgrades or migrations
Strategy 5: Role-Specific Instructions for Better Legal Hold Compliance
Not all custodians need identical hold notices. Sophisticated organizations tailor hold communications to custodian roles and responsibilities.
Differentiated Hold Notices
Consider these variations:
Executive-Level Hold Notice
- Emphasizes the serious legal implications
- References board-level governance responsibilities
- Includes a direct reporting requirement to the chief counsel
- Addresses personal devices and home storage
Department Head Hold Notice
- Addresses team-wide responsibilities
- Requires certification of team-wide compliance
- Addresses departmental shared drives and repositories
- Includes delegation of responsibility to direct reports
Individual Contributor Hold Notice
- Focuses on specific documents/communications relevant to the role
- Provides concrete examples of what must be preserved
- Includes step-by-step preservation instructions
- Clear deadline for acknowledgment
IT/Records Management Hold Notice
- Provides technical requirements
- Addresses system-level implementations
- Requires confirmation of technical completeness
- Includes monitoring and verification procedures
Preservation Instructions Specificity
Clear instructions make all the difference. Rather than “preserve litigation-related materials,” provide specificity:
“You must preserve:
- All emails from your Gmail account with subject lines containing [specific keywords] or involving parties [X, Y, Z]
- All documents in your OneDrive/personal file shares relating to [specific project/transaction]
- All instant messages in Slack channels: [list channels]
- All text messages from your mobile device involving [specific persons]
- All versions of documents you created or modified relating to [specific topic], including deleted versions”
This level of specificity demonstrates that legal counsel has actually thought about what information the custodian likely possesses. It also makes compliance significantly easier for the custodian.
This certification becomes crucial evidence. It demonstrates not just that legal issued a hold, but that IT actually implemented it. Without IT documentation, a hold notice alone proves nothing about actual preservation.
Strategy 6: Continuous Monitoring and Audits for Litigation Readiness
A defensible legal hold doesn’t end with issuance. It requires ongoing verification that the hold remains in place and custodians continue complying. These regular reviews align with litigation hold best practices and ensure organizations remain prepared when responding to litigation holds.
Quarterly Audit Protocols
Sophisticated organizations implement quarterly audits examining:
1. Custodian Compliance
- Which custodians have confirmed receipt of hold notice?
- Have any custodians reported issues?
- Do preservation methodologies remain adequate?
- Have any custodians been terminated (requiring hold termination)?
2. System Compliance
- Are email holds still active?
- Are backup systems functioning?
- Are file deletions still restricted?
- Have any system upgrades affected holds?
3. Scope Appropriateness
- Is the current hold scope still appropriate?
- Should the hold be expanded or narrowed?
- Have new custodians emerged who should be included?
- Are any included custodians no longer relevant?
4. Legal Developments
- Have discovery requests expanded or narrowed the scope?
- Have court orders modified hold requirements?
- Has the litigation status changed?
Certification and Attestation
Organizations should require quarterly certifications:
- From counsel – Confirming that the hold remains necessary and appropriately scoped
- From IT – Confirming that preservation measures remain active and effective
- From custodians – Confirming that they continue complying with hold obligations
These certifications become evidence of continuous, systematic attention to hold obligations.
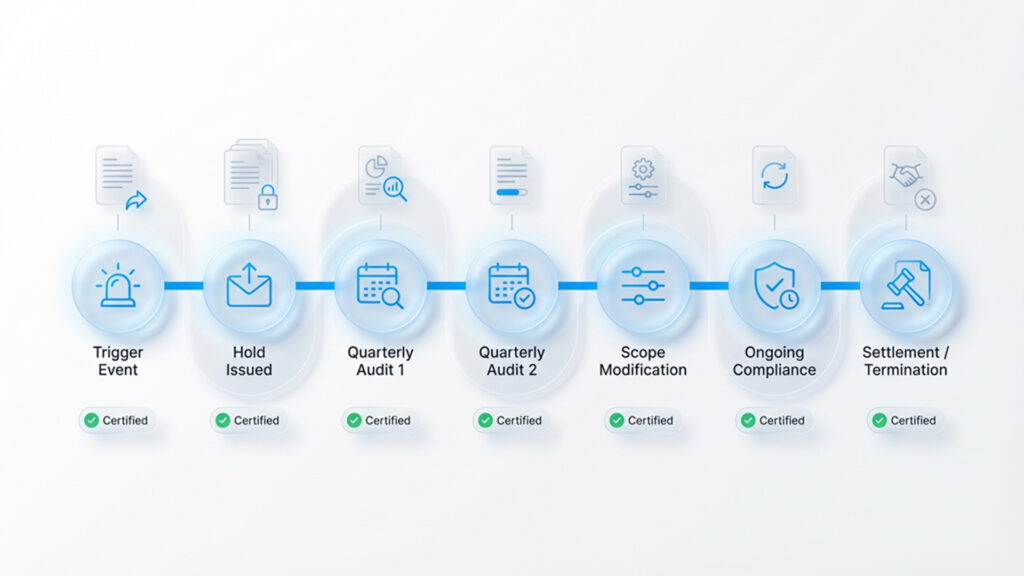
Documentation Trail Creation
Each audit should be documented with:
- Audit date and person conducting the audit
- Custodians verified as compliant
- Any issues identified
- Remedial actions taken
- Recommendations for hold modification
- Attestation signatures
This creates an unmistakable evidence trail demonstrating that the organization took hold obligations seriously throughout the litigation lifecycle, not just at issuance.
Strategy 7: Structured Termination within the Legal Hold Procedure
Ending a legal hold requires the same rigor as initiating one. Poor termination practices can trigger ediscovery sanctions and weaken corporate governance litigation standing.
Termination Decision Documentation
Hold termination decisions should include:
1. Reason for Termination
- Case settlement – Document settlement language
- Case dismissal – Reference court order
- Matter resolution – Document the resolution
- Statute of limitations – Document date calculations
2. Scope Verification
- Confirm all discovery obligations have been met
- Verify all produced documents remain accessible
- Confirm no live litigation obligations remain
- Address any insurance or regulatory retention requirements
3. Approval Mechanism
- Who approved termination?
- What is their authority?
- Did opposing counsel agree?
- Did courts need to approve?
4. Custodian Communication
- Send a written termination notice to all custodians
- Explain why the hold is being terminated
- Address ongoing retention for produced documents
- Provide guidance on document destruction (if applicable)
5. System Verification
- Confirm IT removes hold flags from systems
- Verify email systems resume normal deletion
- Confirm file restrictions are removed
- Document system-level confirmation of hold removal
The Premature Termination Trap
A common defensibility failure: terminating holds too early. Consider this scenario:

This sequence has triggered massive ediscovery sanctions. The lesson: holds should only terminate when there is complete certainty that all litigation and regulatory obligations have ended.
Strategy 8: Communication Tracking for Strong Legal Defensibility
Maintaining records of all communications strengthens legal hold compliance and supports the steps for defensible preservation legal holds framework.
Communications to Archive
Maintain organized records of:
1. Trigger Communications
- Email from business teams alerting legal to a potential dispute
- Correspondence with counsel discussing litigation risks
- Internal legal memos analyzing the necessity of hold
- Board/executive communications regarding holds
2. Hold Issuance Communications
- Draft hold notices with revisions
- Hold notices as issued
- Distribution lists
- Delivery confirmations
- Responses from custodians
- Questions from custodians and responses
3. Modification Communications
- Emails recommending hold modifications
- Expansion notices adding custodians
- Narrowing notices reducing scope
- Court orders affecting hold scope
- Approval emails for modifications
4. Compliance Communications
- IT implementation confirmations
- Custodian compliance certifications
- Audit results and findings
- Remediation communications addressing gaps
5. External Communications
- Correspondence with opposing counsel about holds
- Court submissions mentioning holds
- Third-party communications (cloud providers, IT vendors)
- Responses to discovery requests about preservation
Organization and Retrieval
These records should be organized so that:
- They’re easily retrievable when litigation is active
- The chronological sequence is clear
- Different categories are distinguished
- Sensitive materials (attorney-client privilege, work product) are clearly identified
- Chain of custody is maintained if the records are later produced
Many organizations maintain a litigation management database or hold system specifically for organizing these materials.
Strategy 9: Managing Edge Cases in the eDiscovery Legal Hold Lifecycle
Sophisticated hold procedures anticipate and address complications that arise in practice to maintain litigation readiness.
Employee Termination During Active Hold
When a custodian is terminated while a hold is active:
- Preserve all company-controlled data immediately
- Retrieve all company devices before employee departure
- Address personal devices used for work
- Document all preservation steps
- Communicate with the employee about ongoing obligations
- Restrict access to company systems to preserve integrity
Custodian Death or Incapacity
If a custodian becomes unavailable:
- Identify successor custodian (typically supervisor)
- Determine where the custodian’s documents are stored
- Assess whether the hold should extend to the successor
- Document decisions made
- Address personal devices or home-stored materials
M&A or Corporate Restructuring
When companies merge or reorganize:
- Identify impacts on the custodian structure
- Determine whether merged entity inherits holds
- Expand hold to include transferred data
- Update custodian lists and notifications
- Coordinate holds across multiple entities
Data Breach or Loss Events
If hold-covered data is compromised:
- Immediately notify legal counsel
- Assess the impact on the ability to preserve
- Document what data was lost
- Consider supplemental preservation measures
- Communicate with IT about remediation
- Preserve all evidence related to the breach
International and Multi-Jurisdictional Litigation
Holds in multiple jurisdictions require:
- Identification of jurisdiction-specific hold requirements
- Compliance with local data protection laws (GDPR, etc.)
- Address different standards for “reasonably anticipated” litigation
- Coordinate holds across multiple countries
- Address privilege differences between jurisdictions
Third-Party Custodians
When relevant information is held by third parties:
- Identify all third-party custodians (vendors, partners, service providers)
- Issue separate holds with vendor-specific language
- Address vendor service agreements and limitations
- Coordinate preservation across vendors
- Obtain vendor certifications of compliance
- Document any vendor limitations or refusals
Strategy 10: Automating Legal Hold Workflows with Legal Hold Software
Adopting legal hold software is the most effective way to scale litigation hold best practices. Automation enhances legal defensibility, ensures consistent legal hold compliance, and reduces operational burden.
Legal Hold Platform Benefits
Modern legal hold platforms provide:
Centralized Management Dashboard
- Create, track, and manage holds from a single platform
- View all active holds and status
- Identify hold expiration dates
- Track custodian acknowledgments
- Monitor compliance metrics
Automated Custodian Notification
- Generate customized hold notices
- Automatically deliver via email
- Track delivery and opens
- Request electronic acknowledgments
- Send automatic reminders
Template Management
- Maintain a library of hold notice templates
- Customize templates for matter type
- Ensure consistent, sophisticated language
- Version control changes
- Quickly generate new notices
Documentation Automation
- Automatically create hold file entries
- Timestamped decision records
- Metadata capture (who, when, why)
- Audit trail creation
- Evidence preservation
IT Integration
- Coordinate with email systems (Exchange, Gmail)
- Interface with backup systems
- Manage hold flags in systems
- Obtain technical compliance certifications
- Verify hold status in real-time
Compliance Monitoring
- Track custodian compliance rates
- Identify non-responsive custodians
- Generate compliance reports
- Automate audit procedures
- Create periodic certifications
The Defensibility Advantage of Automation
Automated platforms provide profound defensibility advantages:
- Consistency – Same procedures applied to every hold
- Timeliness – Holds executed immediately without delay
- Documentation – Contemporaneous records automatically created
- Auditability – Complete activity logs and timestamps
- Scalability – Manages dozens or hundreds of simultaneous holds
- Expertise – Built-in legal best practices for in-house counsel
- Evidence – Platform activity logs demonstrate systematic compliance
When courts examine a litigation hold executed through a sophisticated platform, with automatic documentation, timestamps, and IT integration, the defensibility is substantially stronger than a hold managed through email and spreadsheets.
Putting It All Together: A Hypothetical Legal Hold Excellence Case Study
Consider how a sophisticated organization applies these ten strategies:
Day 1 – Trigger Recognition
The finance department notifies legal of a potential dispute with the supplier. Legal immediately analyzes whether litigation is reasonably anticipated and determines it is (Strategy 1). They issue a hold decision memo documenting their reasoning (Strategy 3).
Day 2 – Hold Issuance
Legal identifies all relevant custodians through organizational review and communications analysis (Strategy 2). They draft customized hold notices for different custodian groups (Strategy 5). They coordinate with IT, providing specific technical requirements (Strategy 4). They maintain complete records of all communications (Strategy 8).
Day 3-5 – Implementation and Verification
IT implements holds in the email system, backup systems, and file shares. IT provides written certification of implementation (Strategy 4). All custodians acknowledge receipt of hold notices. Counsel documents all compliance confirmations.
Day 8-30 – Ongoing Management
Legal monitors for special circumstances (employee termination, data issues) and addresses them systematically (Strategy 9). They implement periodic audit procedures (Strategy 6). They maintain complete documentation of all developments.
Month 6 – Litigation Commencement
The case is actually filed. Legal issues modified hold notice expanding scope based on complaint allegations. They coordinate with IT on expanded preservation measures. They update the custodian list. They document all modifications with approvals and reasoning.
Month 9-12 – Continuous Oversight
Quarterly audits confirm that holds remain in place and are effective. Certifications are obtained from legal, IT, and custodians. Any gaps are immediately addressed. Opposing counsel can find no credible basis to challenge the hold’s adequacy.
Month 18 – Settlement
Case settles. Legal carefully documents settlement terms. They obtain approvals before terminating holds. They issue termination notices to all custodians explaining why the hold is ending. They verify that IT removes hold flags. They document that the hold was maintained from reasonable anticipation through settlement.
Litigation Outcome
If ever challenged, the organization can produce complete contemporaneous documentation showing:
- Systematic, documented hold decision process
- Clear communication to all stakeholders
- IT implementation and verification
- Continuous monitoring and improvement
- Compliance with all court orders
- Careful, justified termination decision
This defensible hold process dramatically reduces litigation risk while also demonstrating sophisticated legal governance, a signal of organizational maturity that often facilitates favorable settlement outcomes.
Common Legal Hold Mistakes and How to Avoid Them
Organizations often struggle when responding to litigation holds due to:
Mistake #1: Assuming Hold Notices Are Self-Executing
The Mistake: Legal issues hold notice and assume custodians will comply.
The Reality: Without IT coordination, email systems continue to delete messages. Without management follow-up, many custodians never acknowledge receipt. Without verification, no one confirms that preservation actually occurred.
The Solution: Implement Strategy 4 (IT Integration) and Strategy 6 (Monitoring). Verify that preservation measures are actually in place, not just theoretically issued.
Mistake #2: Over-Inclusive Holds That Expire
The Mistake: Issuing extremely broad holds that capture far more information than necessary.
The Reality: Broad holds are burdensome and invite non-compliance. Custodians can’t reasonably comply with “preserve all potentially relevant information.”
The Solution: Implement Strategy 5 (Role-Specific, Detailed Instructions). More specific holds are both more defensible and more likely to be followed.
Mistake #3: Failing to Document the Hold Decision
The Mistake: Issuing hold notices without creating contemporaneous documentation of why the hold was necessary.
The Reality: When challenged months later, counsel can’t explain the analysis that justified the hold’s scope.
The Solution: Implement Strategy 3 (Detailed Documentation). Create a hold file at the moment of issuance documenting the reasoning behind the hold decision.
Mistake #4: Neglecting New Custodians as Cases Evolve
The Mistake: Issuing a hold, then failing to add custodians as the case scope expands.
The Reality: Critical information from important custodians is lost because they were never placed on hold.
The Solution: Implement Strategy 6 (Ongoing Monitoring and Audits). Regularly reassess whether the hold scope remains appropriate.
Mistake #5: Permitting Holds to Expire Without Active Decision
The Mistake: Holds remain in effect indefinitely or expire automatically without approval.
The Reality: Either preservation continues unnecessarily (burdening IT) or preservation lapses without a proper termination decision.
The Solution: Implement Strategy 6 (Periodic Review). Establish a system requiring quarterly review and active confirmation that holds should continue.
Mistake #6: Failing to Preserve Before Hold Issuance
The Mistake: Waiting until formally issuing a hold to implement preservation.
The Reality: Documents are deleted between the trigger event and hold issuance.
The Solution: Implement emergency preservation measures immediately upon recognition of a litigation trigger, before a formal hold is issued. Issue a formal hold within 24-48 hours, but begin preservation immediately.
Mistake #7: Not Addressing Non-Company Devices
The Mistake: Placing a hold only on company email and systems.
The Reality: Significant communications occurred on personal devices and accounts.
The Solution: Implement Strategy 2 (Comprehensive Custodian Notification). Hold notices should explicitly address personal devices and accounts used for work.
Legal Hold Defensibility: The Judicial Perspective
Understanding how courts evaluate legal holds helps organizations structure defensible processes.
The Standard: What Courts Look For
Courts examining legal hold defensibility ask:
- Was Hold Timely? Did the organization issue a hold upon reasonable anticipation of litigation, not months later?
- Was Scope Reasonable? Did the hold cover relevant parties and information without being absurdly overbroad?
- Was the Communication Clear? Did custodians receive unambiguous notice of what must be preserved?
- Was Compliance Verified? Did the organization confirm that custodians actually preserved information?
- Was the Documentation Complete? Does the organization have contemporaneous records demonstrating the hold process?
- Were Issues Addressed? If problems arose (custodian non-compliance, technical failures), were they documented and remedied?
- Was Hold Maintained? Throughout the litigation, did the organization continue the hold despite operational burdens?
Organizations addressing all seven factors demonstrate defensibility. Those addressing only one or two face vulnerability.
Actual Case Language
Courts examining holds often reference these factors. From actual decisions:
“The party’s failure to issue a litigation hold until three months after the trigger event raises questions about the adequacy of its preservation efforts.”
“The absence of any documentation regarding the decision to narrow the hold scope suggests the modification was not reasoned but reactive.”
“The party’s own IT manager testified that no one confirmed the hold was actually implemented, raising serious questions about the hold’s effectiveness.”
“The organization’s contemporaneous hold file, with detailed reasoning for scope decisions and monthly certifications of compliance, demonstrates systematic attention to preservation obligations.”
These actual judicial statements underscore the importance of defensible processes.
The Regulatory and Compliance Context
Understanding the broader regulatory environment helps organizations structure appropriate holds.
FRCP 37(e) Safe Harbor
Federal Rule of Civil Procedure 37(e) established a safe harbor for parties with reasonable preservation policies:
“Absent exceptional circumstances, a court may not impose sanctions under these rules on a party for failing to provide electronically stored information lost as a result of the routine, good-faith operation of an electronic information system.”
The critical requirement: “routine, good-faith operation” and a “reasonable preservation policy.”
What Constitutes “Reasonable Policy”?
Courts evaluate reasonableness based on:
- Whether the organization had a litigation hold policy
- Whether policies were consistently applied
- Whether policies reflected industry standards
- Whether custodians received training
- Whether processes were documented
- Whether compliance was monitored
Organizations implementing these ten strategies clearly demonstrate reasonable preservation policies. Those who don’t invite challenge.
Other Regulatory Standards
Beyond FRCP 37(e), organizations face holds under:
- State Rules of Civil Procedure – Similar to FRCP
- HIPAA – Healthcare organizations must preserve patient information
- GLBA – Financial institutions must preserve customer data
- SOX – Public companies must preserve business records
- Dodd-Frank – Financial organizations must preserve communications
Each regulatory regime imposes specific preservation obligations that legal holds must address.
Turning Legal Hold into Strategic Litigation Readiness
FREQUENTLY ASKED QUESTIONS (FAQ)
What exactly is a legal hold and when does it become necessary?
A legal hold (also called litigation hold) is a legal obligation to preserve all documents and data that may be relevant to reasonably anticipated litigation or government investigation. It becomes necessary when litigation is “reasonably anticipated”, not when a lawsuit is actually filed, but when the organization is aware of circumstances suggesting litigation may occur.
What are the consequences of failing to maintain a defensible legal hold?
Consequences range from significant to catastrophic. Monetary sanctions can exceed $5 million per case. More damaging are “adverse inferences”, where courts instruct juries to assume destroyed documents were unfavorable to the party that failed to preserve them. This inference alone can lose cases. In extreme cases, courts have dismissed cases entirely for spoliation.
Who is responsible for ensuring a legal hold is implemented and maintained?
Responsibility is shared: Legal counsel initiates the hold decision and issues hold notices; in-house or outside counsel oversees the process; executive leadership ensures organizational commitment and resource allocation; IT implements technical preservation measures; Records management coordinates system-wide compliance; and custodians are responsible for complying with preservation obligations. When responsibility is unclear, holds often fail. Best practice organizations establish a Legal Hold Committee or designate a single accountable party.
Can a legal hold be terminated early, and what standard should be used?
Legal holds can be terminated when no reasonable basis exists to anticipate that litigation will occur, or when concluded litigation has been fully resolved. Holds should not be terminated merely because they’re inconvenient. Premature termination has triggered sanctions. Best practice: obtain approval from multiple parties (legal, IT, sometimes outside counsel) before terminating. Document the reason for termination. If the matter is later revived, you must be able to explain why the original hold was appropriately terminated.
How does a legal hold apply to personal devices and non-company accounts?
Modern holds must address personal devices and accounts. If a custodian uses personal email, phones, or home computers for work communications, the hold applies. Hold notices should explicitly address: personal email accounts used for work, personal phones and tablets, home computers with work files, personal cloud storage, and personal messaging applications. The challenge is enforcement, you can’t directly control personal devices. Strategies include: requiring employees to preserve and potentially produce personal device data, implementing bring-your-own-device policies, or accepting that some relevant data may not be perfectly preserved.
What should a legal hold documentation file contain?
A defensible legal hold file should include: (1) trigger documentation explaining why litigation was reasonably anticipated; (2) scope determination documenting what is covered and why; (3) custodian identification and reasoning; (4) hold notices as issued; (5) distribution confirmations; (6) custodian acknowledgments; (7) IT implementation certifications; (8) any modifications with documentation of reasons; (9) quarterly audit results; (10) compliance verifications from legal, IT, and custodians; (11) communications with opposing counsel; and (12) termination decision and documentation. This complete record becomes your evidence of systematic, reasoned hold management.
How often should legal holds be reviewed and updated?
Best practice calls for quarterly reviews (or more frequently in active litigation). Each review should assess: whether the hold scope remains appropriate, whether new custodians should be added, whether any custodians are no longer relevant, whether IT systems remain compliant, whether any court orders have expanded/narrowed scope, and whether any special circumstances have arisen. Many organizations synchronize reviews with litigation developments or case status conferences. Documentation of these periodic reviews becomes crucial evidence of continuous compliance.
What is the relationship between legal holds and litigation discovery obligations?
A legal hold is the preservation obligation; discovery is the production obligation. A legal hold says “preserve this information.” Discovery says, “produce this information to opposing parties.” While related, they’re distinct. You might preserve information under a hold but not produce it because it’s protected by privilege or attorney work product. Conversely, you might produce information that wasn’t originally under hold if it becomes relevant as the case develops. Both obligations require careful management.
Can an organization rely on automatic system deletion policies (like email auto-deletion) once a hold is issued?
No. A critical aspect of Strategy 4 (IT Integration) is ensuring that automatic deletion systems are disabled or overridden for hold-covered information. Email systems that automatically delete messages after 90 days must be configured to preserve hold-flagged messages indefinitely. Backup retention policies must be modified if they would delete relevant data. Any automatic process that would result in the destruction of hold-covered information must be disabled or, if disabled automatically, regularly verified as remaining disabled. The organization cannot rely on “we have policies preventing destruction” without confirming that those policies are actually preventing the destruction of hold-covered data.
What role does technology play in making legal holds more defensible?
Technology is increasingly important to hold defensibility. Modern legal hold platforms provide: contemporaneous documentation (timestamped records created as holds are issued), consistency (same procedures applied to every hold), IT integration (direct communication with email and file systems), monitoring (real-time verification of hold compliance), and auditability (complete activity logs). When courts compare a hold managed through email and spreadsheets (error-prone, difficult to verify) with a hold managed through a sophisticated platform (documented, verified, integrated), the technology-managed hold is substantially more defensible. Additionally, platform documentation creates stronger evidence of systematic compliance.
What should organizations do if they discover that a legal hold was not properly implemented?
First, immediately notify counsel if the problem involves potential litigation exposure. Second, determine the scope of the failure, which custodians/systems were affected and for how long? Third, implement supplemental preservation immediately to stop any ongoing destruction. Fourth, attempt to recover destroyed data (often possible through IT backup systems or custodian recovery). Fifth, document the failure and remedial measures taken. Finally, disclose the problem to opposing counsel and the court if litigation is active. While failures are serious, prompt remediation and transparent disclosure mitigate consequences. Attempting to conceal hold failures typically makes matters worse.
How do legal holds interact with data privacy laws like GDPR?
Legal holds can conflict with data privacy obligations that require data deletion. GDPR and similar laws generally don’t override legal hold obligations, but organizations must balance competing requirements. Strategies include: (1) implementing legal holds specifically and narrowly (GDPR-compliant scoping); (2) applying technical protections limiting access to hold-covered data; (3) obtaining judicial approval for extended retention; (4) seeking consent from data subjects for hold retention; (5) anonymizing data where possible while maintaining relevance. Organizations with international operations should address these conflicts proactively in their legal hold procedures.