In modern litigation, the battle is won or lost before discovery even begins. Success in complex matters hinges on effective planning and, specifically, the execution of a robust Electronically Stored Information (ESI) Protocol.
An ESI Protocol is far more than a technical document; it is the defensibility blueprint for your case. It is the agreed-upon strategy between opposing counsel—or the guiding mandate for in-house teams—that determines how ESI will be identified, preserved, collected, exchanged, and utilized in a matter.
For corporate organizations and their counsel facing complex litigation, relying on outdated or generic ESI protocols is a recipe for sanctions, inflated costs, and lost control.
This comprehensive guide is the definitive resource for formulating an ESI Protocol optimized for the modern digital landscape, anchored by the capabilities of Venio Systems’ unified eDiscovery platform.
1. Understanding the Legal Necessity: Why ESI Protocols Matter
An ESI Protocol operationalizes the Federal Rules of Civil Procedure (FRCP), primarily Rule 26(f) (Discovery Planning) and Rule 34(b) (Specifying Form of Production).
The Risk of a Missing Protocol
Without a specific, negotiated protocol in place, you expose your client to three critical risks:
- Spoliation Sanctions (Rule 37(e)): A vague protocol increases the risk of inadvertent loss or destruction of relevant ESI, leading to severe sanctions.
- “Clash of the Forms”: Opposing counsel may demand production in a format (e.g., native with all metadata) that is overly burdensome or irrelevant, forcing costly, protracted negotiations.
- Lack of Proportionality (Rule 26(b)(1)): Without agreed-upon limits, the scope of discovery can explode, turning a manageable case into an unmanageable financial burden.
The ESI Protocol vs. The Preservation Notice
It’s critical to distinguish:

2. The Seven Pillars of a Modern ESI Protocol
A successful protocol is detailed, proportional, and technologically informed. It must address seven key areas, moving from the legal scope to the technical implementation.
Pillar 1: Scope & Custodianship
Define the outer boundaries of the search.
- Custodians: Clearly list all individuals whose ESI is relevant (including former employees, if applicable).
- Date Ranges: Specify the exact start and end dates for ESI relevance, ensuring this scope aligns with the principle of proportionality.
- Data Locations: Explicitly list the types of repositories (e.g., corporate email, file shares, specific SharePoint sites, mobile devices).
Pillar 2: Identification of Data Sources (Traditional vs. Modern ESI)
This is the most crucial area for modern litigation. Your protocol must go beyond basic email.
- Traditional: Corporate Email (Exchange, Gmail), Network File Shares, Document Management Systems (DMS).
- Modern (Venio’s Focus): Cloud Services (AWS, Azure, Google Cloud), Collaboration Tools (Slack, Teams, Zoom Chat), Mobile Data (Text Messages, App Data), and IoT/Specialized Databases.
Venio Systems Advantage: The Venio platform uses specialized connectors to seamlessly integrate with and forensically collect complex modern ESI (like Slack, Teams, and cloud repositories), ensuring your protocol covers all bases without sacrificing data integrity.
Pillar 3: Search Methodology and Filtering (Proportionality)
This section details how the data volume will be reduced to meet proportionality requirements.
- Keywords: Agree on search terms (and their syntax—e.g., proximity searches, Boolean operators). Documenting this process within the protocol is key to defensibility.
- De-duplication: Specify whether you will use Global (across all custodians) or Custodian-level de-duplication. Venio’s processing engine handles both with auditable reports.
- Date/File Type Filtering: Agree on removing clearly irrelevant file types (e.g., executable files, system files) or content falling outside the agreed-upon date range.
Pillar 4: Production Format (The Technical Standard)
The protocol must specify the format of the exchanged documents, which impacts admissibility and review costs.

Pillar 5: Metadata Fields
Metadata (the data about the data) is non-negotiable ESI. The protocol must specify exactly which metadata fields will be produced with the ESI.
- Common Fields: Author, Date Created, Date Sent, Date Last Modified.
- Critical Modern Fields: Conversation thread ID (for chats), participants (for collaboration tools), and hash values (for verification).
Venio Defensibility: Every file processed and produced by Venio maintains a forensic-grade audit trail and verifiable hash values, providing the detailed metadata required by the protocol without requiring custom tools.
Pillar 6: Handling Privilege and Logistical Issues
How will the parties handle inadvertently produced privileged documents?
- Clawback Agreement: Specify a process (often under FRE 502(d)) where inadvertently produced privileged material can be “clawed back” without waiving privilege.
- Confidentiality: Detail the confidentiality designations (e.g., “Confidential,” “Attorneys’ Eyes Only”) and how they will be stamped on the produced documents.
Pillar 7: Production Logistics
Define the technical exchange method.
- Media: Hard drive, secured file transfer service, or cloud-to-cloud transfer.
- Load File: Specify the required load file format (e.g., industry-standard DAT/OPT, or custom JSON/XML) used to load the produced ESI into the opposing counsel’s review platform.
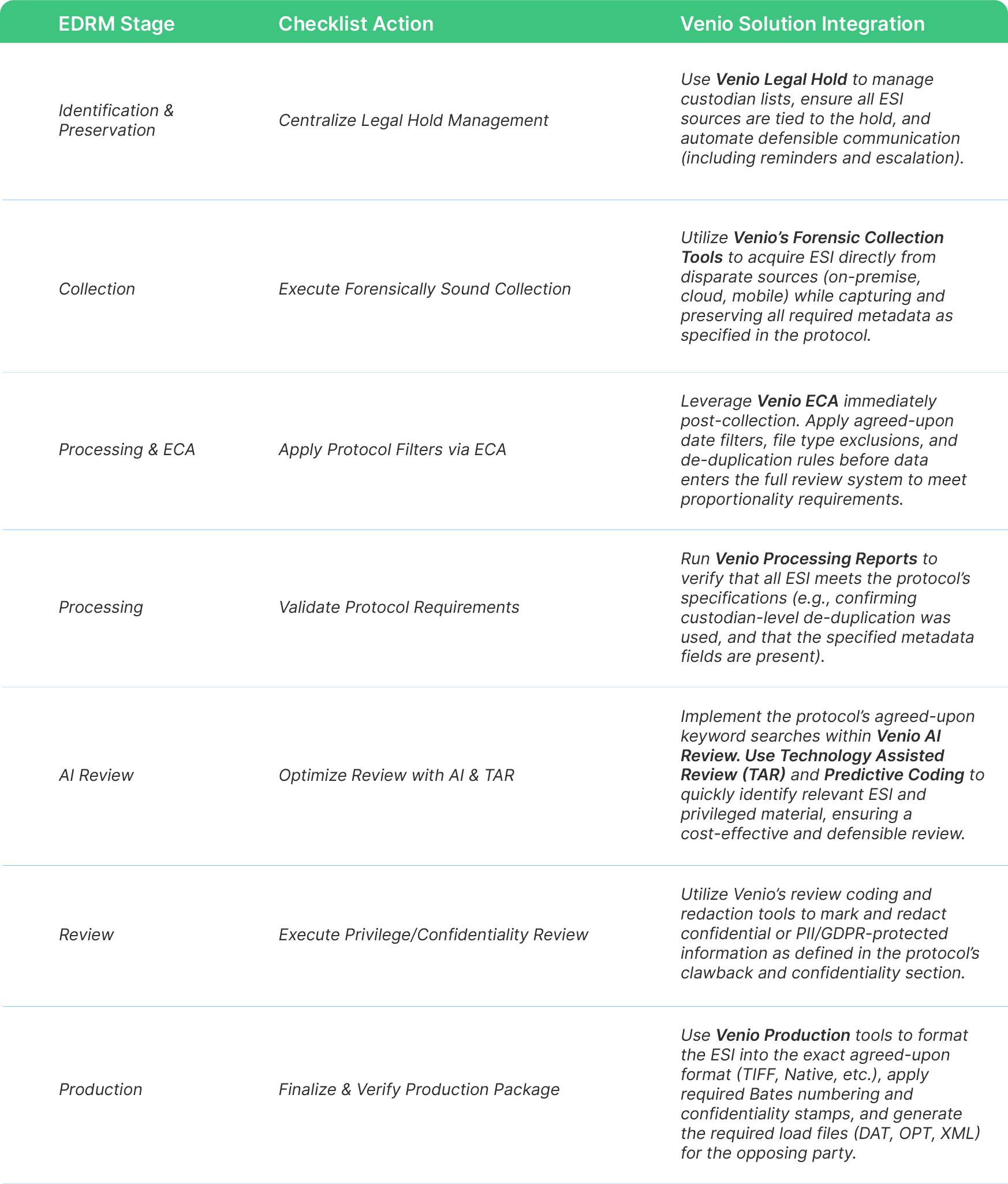
3. The ESI Protocol Implementation Checklist (Venio-Powered Strategy)
Formulating the ESI Protocol is only the first step. Execution requires technology that can enforce the agreed-upon terms defensibly and efficiently.
Here is the Venio-optimized 7-Step Checklist for implementing the agreed-upon ESI Protocol.
4. Advanced Protocol Challenges: Solving the Modern Data Gaps
Competitor protocols often fail because they ignore the complexity of modern data. Your Venio-powered ESI Protocol must specifically address these challenges.
Challenge A: Collaboration Data (Slack, Teams, Zoom)
Collaboration platforms are transactional, containing highly volatile, non-linear data.
- Protocol Requirement: The ESI Protocol must specify the format of production (e.g., flattened HTML or native threads) and require the preservation of conversation threading and participant metadata.
- Venio Solution: Our specialized connectors capture this data in context, allowing it to be reviewed and produced as continuous conversations rather than fragmented messages, which is vital for judicial clarity.
Challenge B: Mobile Device Data
Mobile ESI is complex because it includes text messages, third-party application data (e.g., WhatsApp), and device logs.
- Protocol Requirement: The protocol should define whether you are collecting the entire device image (forensically sound) or only specific data types (e.g., SMS/MMS messages) to ensure proportionality.
- Venio Solution: Venio’s forensic tools support defensible, targeted mobile collection, allowing you to meet the protocol’s narrow requirements without over-collecting personal data.
Challenge C: Data Privacy and Cross-Border ESI
If the case involves global data (GDPR, CCPA, PII), the ESI Protocol must act as a bridge between eDiscovery and privacy compliance.
- Protocol Requirement: Include a section on data handling that details the process for redaction of PII and specifies the legal basis (e.g., Transfer Impact Assessment) for cross-border data transfer if ESI needs to leave the country of origin.
- Venio Solution: Venio’s integrated review tools include built-in PII and entity recognition features, streamlining the process of identifying and redacting sensitive data to ensure your production is compliant with both discovery and privacy laws.
Conclusion: The ESI Protocol as Your Strategic Asset
An ESI Protocol is not a burden; it is your firm’s most potent strategic asset in eDiscovery. When formulated correctly, it controls the scope, ensures defensibility, and guarantees cost predictability.
By leveraging the power of a unified platform like Venio Systems, you transform the theoretical ESI Protocol into a powerful, automated, and auditable reality. This approach allows your legal team to focus on the merits of the case, secure in the knowledge that your ESI management is sound, proportional, and technologically advanced.
Stop losing time and money wrestling with outdated ESI concepts. Start leading your matters with a technologically optimized ESI Protocol.
Managing Electronically Stored Information (ESI) defensibly is the single biggest challenge in litigation. Manual processes, fragmented data, and missed metadata lead to sanctions and massive costs.
The Venio Systems unified platform simplifies every stage of the EDRM—from Legal Hold to AI-Powered Review—ensuring proportionality and defensibility while cutting your total eDiscovery spend.
Key Features:
✅ Unified platform for the entire EDRM.
✅ Forensics-grade collection for complex ESI sources.
✅ AI & ECA to drastically reduce review volume.
✅ Guaranteed defensibility and chain of custody.
Frequently Asked Questions: ESI Protocol Clarified
While the principles of an ESI Protocol are essential, the technical details can often lead to confusion. Here we address some of the most common questions legal teams have when formulating a modern, defensible protocol.
1. What is the fundamental difference between an ESI Protocol and a Legal Hold Notice?
This distinction is crucial. The Legal Hold Notice is a preservation order telling custodians what data must be saved and instructing them not to delete it. The ESI Protocol, conversely, is a discovery agreement that specifies how that saved ESI will be searched, formatted, and exchanged with opposing counsel.
While preservation is the initial step, the protocol formalizes the technical obligations. Venio Legal Hold software centralizes the preservation duty, while the Venio platform enforces the protocol’s technical specifications (like format and load file requirements) during the downstream processing and production stages.
2. How does an ESI Protocol address proportionality under FRCP Rule 26?
An effective ESI Protocol is the primary mechanism for meeting the proportionality requirement of FRCP Rule 26. It does this by mutually agreeing on limitations before costly collection and review begin. This should include defining narrow date ranges, specific custodian scope, precise keyword lists, and the exclusion of clearly irrelevant file types (e.g., system files).
Venio ECA (Early Case Assessment) is critical here. It allows you to implement these agreed-upon protocol filters immediately post-collection, cutting the irrelevant data volume before it impacts your expensive review phase.
3. Can an ESI Protocol cover complex modern data sources like Slack, Microsoft Teams, or mobile devices?
Yes, it absolutely must. A modern ESI Protocol must include specific stipulations for collaboration platforms and mobile ESI because these sources contain unique and crucial metadata (such as conversation threading, reaction emojis, and participant lists) that is easily lost during standard collection.
If your protocol ignores these sources, you expose yourself to sanctions. Venio Systems utilizes specialized connectors to defensibly acquire and normalize data from these complex sources, ensuring the data produced complies precisely with the agreed-upon protocol and preserves the conversational context.
4. What are the risks of using a generic, templated ESI Protocol?
Generic, templated protocols are a significant risk. They are a one-size-fits-all approach that fails to account for case-specific data architecture (e.g., your specific cloud providers or document management systems). This often leads to two major problems:
- Gaps: Key modern data sources or specific custodians are accidentally omitted, leading to inadvertent spoliation.
- Over-production: The template requires the production of unnecessarily broad data sets (like all metadata), inflating costs.
A bespoke protocol, informed by thorough data mapping and executed through a unified platform like Venio, is the safest way to minimize sanctions risk and maintain defensibility.
5. Which specific metadata fields should an ESI Protocol mandate for production?
While the basics (Date Created, Date Sent) are standard, a modern ESI Protocol should mandate production of specific metadata fields essential for proving authenticity and context. These include:
- MD5/SHA Hash Value: For integrity and verification (chain of custody).
- Conversation ID or Threading ID: Crucial for linking messages in collaboration apps.
- Date Last Accessed/Modified: Essential for timeline reconstruction.
The Venio platform is engineered to automatically preserve, process, and produce all required native metadata fields, ensuring your production package meets even the strictest protocol demands without manual intervention.